Lecture 9 ~ Intrusion Detection System ~
Assalamualaikum w.b.t...
Lecture 9 nie xbyk sgt daaa pn... ermmm... Inie kelas bab Intrusion Detection System.. Hmmm... Topic yg cover lam lecture nie :-
•Intruders
•Security Intrusion & Detection
•Types of IDS
~HIDS
~NIDS
~DIDS
•IDS Techniques
•SNORT
•Honeypots
Intruders
•significant issue hostile/unwanted trespass
~from benign to serious
•user trespass
~unauthorized logon, privilege abuse
•software trespass
~virus, worm, or trojan horse
•classes of intruders:
–masquerader, misfeasor, clandestine user
Examples of Intrusion
•remote root compromise
•web server defacement
•guessing / cracking passwords
•copying viewing sensitive data / databases
•running a packet sniffer
•distributing pirated software
•using an unsecured modem to access net
•impersonating a user to reset password
•using an unattended workstation
Security Intrusion & Detection
~Security Intrusion
a security event, or combination of multiple security events, that constitutes a security incident in which an intruder gains, or attempts to gain, access to a system (or system resource) without having authorization to do so.
~Intrusion Detection
a security service that monitors and analyzes system events for the purpose of finding, and providing real-time or near real-time warning of attempts to access system resources in an unauthorized manner.
Hackers
~motivated by thrill of access and status
•hacking community a strong meritocracy
•status is determined by level of competence
~benign intruders might be tolerable
•do consume resources and may slow performance
•can’t know in advance whether benign or malign
~IDS / IPS / VPNs can help counter
~awareness led to establishment of CERTs
•collect / disseminate vulnerability info / responses
Intrusion Detection Systems
~classify intrusion detection systems (IDSs) as:
•Host-based IDS: monitor single host activity
•Network-based IDS: monitor network traffic
~Logical components:
•sensors - collect data
•analyzers - determine if intrusion has
•occurred
•user interface - manage / direct / view IDS
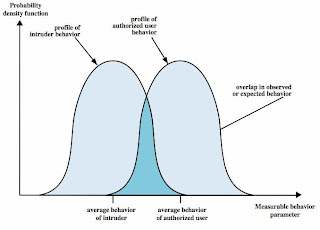
IDS Principles
•assume intruder behavior differs from
•legitimate users
~expect overlap as shown
~observe deviations
•from past history
~problems of:
*false positives
*false negatives
*must compromise
IDS Requirements
•run continually
•be fault tolerant
•resist subversion
•impose a minimal overhead on system
•configured according to system security policies
•adapt to changes in systems and users
•scale to monitor large numbers of systems
•provide graceful degradation of service
•allow dynamic reconfiguration
Types of IDS
•Host IDS
•Network IDS
•Distributed IDS
Host-Based IDS
•specialized software to monitor system activity to
•detect suspicious behavior
~primary purpose is to detect intrusions, log suspicious
~events, and send alerts
~can detect both external and internal intrusions
•two approaches, often used in combination:
~anomaly detection - defines normal/expected behavior
~threshold detection
~profile based
•signature detection - defines proper behavior
Audit Records
•a fundamental tool for intrusion detection
•two variants:
~native audit records - provided by O/S
•always available but may not be optimum
~detection-specific audit records - IDS specific
•additional overhead but specific to IDS task
•often log individual elementary actions
•e.g. may contain fields for: subject, action, object, exception-condition,
resource-usage, time-stamp
Network-Based IDS
~network-based IDS (NIDS)
•monitor traffic at selected points on a network
•in (near) real time to detect intrusion patterns
•may examine network, transport and/or application level protocol activity directed
toward systems
~comprises a number of sensors
•inline (possibly as part of other net device)
•passive (monitors copy of traffic)
NIDS Sensor Deployment

Distributed Host-Based IDS


Intrusion Detection Techniques
~signature detection
•at application, transport, network layers; unexpected application services, policy
violations
~anomaly detection
•of denial of service attacks, scanning, worms
~when potential violation detected sensor sends an alert and logs information
•used by analysis module to refine intrusion detection parameters and algorithms
•by security admin to improve protection
Anomaly Detection
~threshold detection
• checks excessive event occurrences over time
• alone a crude and ineffective intruder detector
• must determine both thresholds and time intervals
~profile based
• characterize past behavior of users / groups
• then detect significant deviations
• based on analysis of audit records
*gather metrics: counter, guage, interval timer, resource utilization
*analyze: mean and standard deviation, multivariate, markov process, time series,
operational model
Signature Detection
~observe events on system and applying a set
~of rules to decide if intruder
~approaches:
•rule-based anomaly detection
*analyze historical audit records for expected behavior, then match with current
behavior
•rule-based penetration identification
*rules identify known penetrations / weaknesses
*often by analyzing attack scripts from Internet
*supplemented with rules from security experts
IDS in the market

Snort
~lightweight IDS
•real-time packet capture and rule analysis
•passive or inline

Snort Rules
~use a simple, flexible rule definition language
~with fixed header and zero or more options
~header includes: action, protocol, source IP, source port, direction, dest IP, dest
port
~many options
~example rule to detect TCP SYN-FIN attack:
Alert tcp $EXTERNAL_NET any -> $HOME_NET any \ (msg: "SCAN SYN FIN"; flags: SF, 12 ; \ reference: arachnids, 198; classtype: attempted-recon;)
Honeypot Deployment
~are decoy systems
-filled with fabricated info
-instrumented with monitors / event loggers
-divert and hold attacker to collect activity info
-without exposing production systems
~initially were single systems
~more recently are/emulate entire networks

Hmm... xbyk sgt kn lecture kiteorg kali nie.. ermm... xla busann sgt... ermmm.. best!...
alhamdulillahh...




0 komplen:
Post a Comment